Web strategies
Design, SEO and customer acquisition

Understanding web development
From design to optimization
Web development encompasses several essential stages in the creation of a high-performance website. It all starts with design, where user needs are analyzed to define the site’s structure and interface. Next, development takes the form of functionality programming, whether for the front-end, visible to the user, or the back-end, which manages data.
Optimization comes last, aiming to improve speed, security and user experience, while guaranteeing good visibility on search engines through SEO. This ongoing process enables us to adapt our sites to technological developments and user expectations.
The keys to UX/UI design

Research and analysis of user needs
This involves understanding user expectations, behaviors and needs through market research, interviews or user testing. This creates a solid foundation for the design of intuitive, adapted interfaces.
Ergonomic interface design
UI (User Interface) focuses on creating aesthetically pleasing and functional interfaces, guaranteeing fluid navigation. This includes the selection of colors, typography, icons and the layout of elements to promote accessibility and legibility.

User experience testing and optimization
UX (User Experience) aims to maximize user satisfaction by optimizing interaction with the product or service. This includes regular testing, user feedback and adjustments to improve the responsiveness, fluidity and relevance of the site or application.
SEO optimization and search engine optimization strategy
SEO positioning
SEO optimization and natural referencing strategy are essential to improve a website’s visibility on search engines.
This involves optimizing both the technical elements of the site, such as loading speed and URL structure, and the content, using relevant keywords and improving the user experience. A good SEO strategy also requires careful attention to backlinks, analysis of site performance, and ongoing adaptation to changes in search engine algorithms. The aim is to increase the site’s relevance in the eyes of search engines, while offering a fluid and intuitive navigation for users.

Fluid customer experience
The keys to success in e-commerce: strategy, customer experience and visibility

Acquisition strategies and tracking
advertising performance
Targeted advertising

Creating ads for qualified
audiences
Managing an advertising campaign involves designing ads tailored to precise audience segments, adjusting budgets in real time and tracking conversions to optimize the acquisition of qualified leads.

Digital remarketing and customer
loyalty
Remarketing on an ad platform relies on the analysis of browsing behavior and the delivery of personalized messages to encourage visitors to return and increase engagement.

Performance analysis and campaign
fine-tuning
Campaign performance analysis is based on conversion indicators, channel identification and ongoing ad optimization to maximize the profitability of advertising investments.
Ongoing technical support and secure hosting
Reliable online presence
Infrastructure management
and server monitoring
Continuous monitoring of the infrastructure to ensure optimal operation and prevent server failures.
Upgrade maintenance and software updates
Carry out regular software updates and enhancements to optimize performance and integrate the latest features.
Site migration and data management
Organize and manage the transfer of data and websites to new servers or hosts, ensuring a smooth transition.
Proactive technical support
and incident resolution
Offer reactive and proactive technical support to detect and resolve problems quickly and avoid service interruptions.
Regular backup and fast
restore
Implement frequent backup strategies to ensure rapid data recovery in the event of loss or disaster.
Enhanced security and access management
Implement strict security protocols to protect sensitive data and control access to systems and servers.
Visual identity creation and
multi-channel branding strategy
Graphic charter

Drawing up a graphic charter for visual consistency
A detailed graphic charter defines the rules for using the logo, colors and typography for a digital services brand, ensuring consistency across all media.

Communication media to enhance image
Print and digital media, such as brochures and e-mail signatures, are designed around a strong visual identity, reinforcing brand recognition.

Brand storytelling to boost engagement
A storytelling campaign highlights the values and history of an artisan company, creating visual and narrative coherence on social networks and the website.
Optimizing your content marketing
Keys to capturing and engaging your audience
In an information-saturated digital world, it’s essential to optimize your content marketing to capture attention and effectively engage your audience.
To do this, you need to create high-quality, relevant and well-targeted content that meets the needs and expectations of your users. The integration of appropriate keywords and the use of captivating storytelling reinforce the impact of the message. What’s more, regular interaction with your audience, whether through comments, surveys or responses on social networks, fosters loyalty and creates a relationship of trust. By using analysis and tracking tools, you can constantly fine-tune your strategy to improve engagement and maximize results.
Key measures to reinforce
IT security
Implementing multi-factor authentication and strong passwords limits the risk of unauthorized access to systems. Regular software updates and cybersecurity training for employees are essential to prevent attacks.
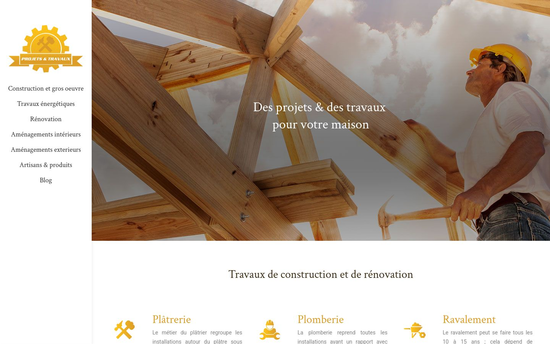
Website design for real estate and construction: digital solutions for a competitive edge
In-depth knowledge of the real estate and construction sectors guarantees the development of appropriate, high-performance websites. Advanced functionality and intuitive design optimize project presentation, customer engagement and online visibility. Website creation for real estate and construction: digital solutions for a competitive edge.